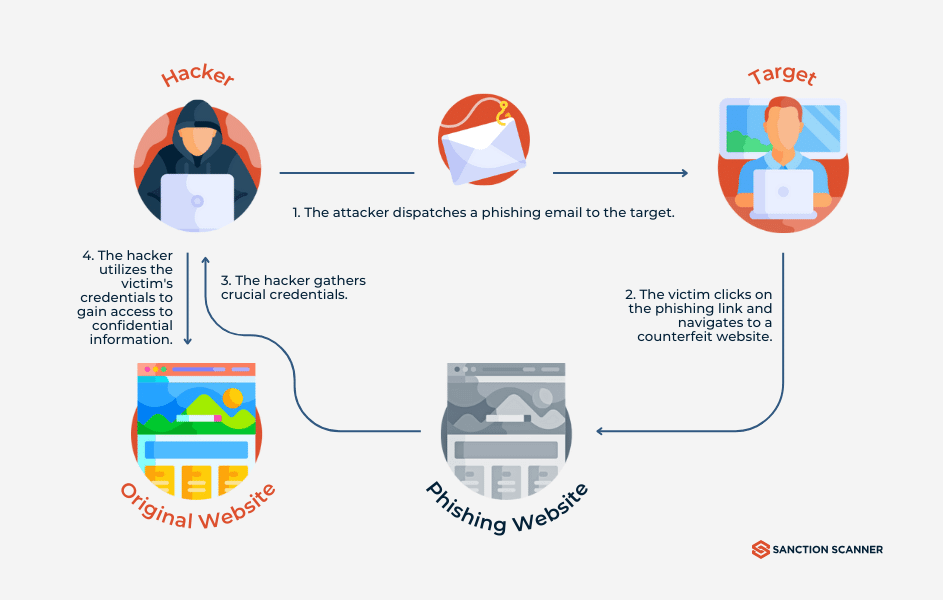
Phishing attacks pose a widespread threat in today's digital world. By impersonating trusted entities through emails and messages, internet pirates aim to trick unsuspecting individuals into revealing account numbers, passwords, social security numbers, and other confidential data. The term "phishing" accurately describes their method of casting out bait to hook valuable information.
The consequences of falling prey to such schemes can be severe. Cybercriminals can exploit stolen information to drain bank accounts, accumulate fraudulent charges on credit cards, and even assume victims' identities, leaving a trail of financial ruin and severed reputations.
Fortunately, there are steps individuals can take to defend against phishing attacks and safeguard their personal and financial well-being. By staying alert and exercising caution when encountering unexpected requests for sensitive information, such as suspicious emails or messages, individuals can thwart phishing attempts before they succeed.
The Impact of Phishing Attacks
The impact of phishing attacks on businesses can be severe, affecting various facets of operations. Financially, businesses suffer significant losses due to the costs associated with mitigating and recovering from attacks, including expenses related to security measures, stock devaluation, and regulatory fines. Moreover, breaches undermine consumer trust and tarnish brand reputation, as customers prioritize doing business with trustworthy entities capable of safeguarding their data.
Additionally, the loss of proprietary data poses a substantial threat, as cybercriminals target valuable information such as trade secrets and upcoming product launches. The disruption of business operations following a breach can hinder essential functions, such as order processing and customer communication, exacerbating the overall impact on productivity and profitability. These multifaceted consequences underscore the urgency for businesses to implement robust cybersecurity measures to mitigate the risks posed by phishing attacks.
Common Types of Phishing Attacks
Malware/Ransomware Attacks
Ransomware attacks, a subset of malware assaults, hold victims' data hostage through encryption, demanding payment for its release. These attacks often use cryptocurrencies like Bitcoin to obscure the identity of cybercriminals. The financial impact is significant, with an average monthly suspected ransomware transaction value surpassing $66 million in 2021 alone. Additionally, projections suggest ransomware-related damages could skyrocket to $265 billion by 2031, highlighting the dire consequences beyond immediate financial losses. Types of ransomware include encrypting ransomware, screen lockers, scareware, doxware, and mobile ransomware, each posing unique threats to victims' data and systems.
Ransomware's rapid evolution and proliferation stem from accessible malware creation tools, enabling cybercriminals to produce new variants swiftly. Furthermore, the rise of online markets for ransomware provides opportunities for both sophisticated hackers and less tech-savvy individuals to engage in cybercrime, exacerbating the threat landscape. These factors underscore the importance of proactive cybersecurity measures to mitigate the risk posed by ransomware attacks.
Link Manipulation
Link manipulation tactics involve phishing attempts where cybercriminals send deceptive links to malicious websites. When clicked, these links redirect users to fraudulent sites, often resembling legitimate ones, to deceive victims into divulging sensitive information. Hovering over links to reveal actual addresses can help users identify and avoid falling victim to link manipulation. This simple yet effective preventive measure empowers individuals to thwart phishing attempts and protect their digital security. As cyber threats continue to evolve, maintaining vigilance and adopting proactive strategies remain paramount in safeguarding against malicious activities like link manipulation.
Spear Phishing
Spear phishing stands as a highly personalized form of cyberattack targeting specific individuals or organizations. Unlike conventional phishing, spear phishing involves tailored emails that appear legitimate to recipients, aiming to elicit sensitive information or infect devices with malware. Perpetrators, including government-sponsored hackers and individual cybercriminals, conduct extensive research on their targets, enabling them to craft convincing messages that exploit social engineering tactics. Even high-ranking targets, such as C-suite executives, can fall victim to these sophisticated attacks, underscoring the effectiveness of spear phishing in breaching organizational defenses.
Clone Phishing
Clone phishing, a subtype of spear phishing, involves replicating legitimate email messages previously received by the recipient. Cybercriminals capitalize on recipients' familiarity with past communications, crafting fraudulent messages to mimic authentic ones. For instance, if a recipient recently received a shipment tracking notification, a clone phishing attack might replicate this message to deceive the recipient. By exploiting trust and familiarity, clone phishing aims to deceive recipients into divulging sensitive information or performing malicious actions, underscoring the need for heightened vigilance and robust cybersecurity measures.
CEO Phishing
CEO phishing exploits the authority and trust associated with senior executives within organizations. Perpetrators impersonate CEOs or other high-ranking officials, leveraging email-based fraud to manipulate staff members into compromising actions. Thorough research enables cybercriminals to craft convincing spear-phishing emails that mimic the CEO's writing style and address recipients by name. Urgency and psychological manipulation coerce recipients into complying with fraudulent requests, such as wire transfers or divulging sensitive information. As CEO phishing targets the heart of organizational trust, raising awareness and implementing stringent authentication measures are crucial in mitigating its impact.
Examples of Phishing Attacks
AOHell, the First Recorded Example
In the early days of the internet, around 1994, a Pennsylvania teenager created a malicious program named AOHell, intending to exploit vulnerabilities in America Online (AOL) accounts. AOHell operated by infiltrating the AOL client, clandestinely extracting user passwords, and fabricating counterfeit accounts to masquerade as legitimate AOL customer service personnel. One of its notable tactics was to prompt unsuspecting users to verify their accounts under the guise of enhancing security, effectively pioneering what would later be recognized as phishing, a deceptive practice aimed at extracting sensitive information from individuals.
The Nordea Bank Incident
In 2007, Swedish banking institution Nordea fell victim to a sophisticated phishing attack, resulting in the loss of over 7 million kronor. Perpetrators orchestrated a widespread email campaign, distributing fraudulent messages equipped with the "haxdoor" Trojan. These emails deceived unsuspecting recipients into installing what appeared to be anti-spam software but was, in reality, a malicious program designed to compromise their systems. The fraudulent scheme, later termed the "biggest ever online bank heist" by cybersecurity experts, successfully installed keyloggers on victims' computers, facilitating the interception of sensitive login credentials.
Operation Phish Phry
The year 2009 marked one of the FBI's most significant cybersecurity operations, dubbed "Operation Phish Phry," aimed at dismantling a sophisticated network of cybercriminals engaged in bank fraud. With operations spanning across the United States and Egypt, the criminal syndicate orchestrated a series of phishing attacks that resulted in the unlawful acquisition of $1.5 million. Former FBI Director Robert Mueller emphasized the escalating threat posed by phishing attempts, acknowledging the necessity of proactive measures to combat evolving cyber threats. Consequently, the establishment of the National Cyber Investigative Joint Task Force signified a concerted effort to enhance cybersecurity strategies and mitigate the impact of cybercrime on financial institutions and individuals.
Detecting and Preventing Phishing Attacks
Detecting and preventing phishing attacks requires a multifaceted approach, combining both organizational and personal strategies. At the organizational level, comprehensive internet security education is paramount. Companies should invest in training programs to educate employees on how to identify phishing attempts effectively. Equipping staff with the knowledge to recognize phishing warning signs empowers them to take proactive measures against potential threats. Additionally, implementing anti-phishing software can serve as a vital line of defense, automatically detecting and blocking phishing scams before they reach employees' inboxes.
On a personal level, individuals can take proactive steps to mitigate the risk of falling victim to phishing scams. Continuous education is key; staying informed about the latest phishing techniques and scams allows individuals to remain vigilant and recognize potential threats. Being skeptical of unsolicited emails and practicing caution before clicking on links or downloading attachments can help individuals avoid falling prey to phishing attempts. By adhering to the principle of "verify before you act," individuals can verify the authenticity of communications from purported companies by contacting them directly through official channels.
Furthermore, adopting proactive cybersecurity measures enhances personal defense against phishing attacks. Utilizing multi-factor authentication (MFA) adds an extra layer of security to online accounts, significantly reducing the risk of unauthorized access. Regularly monitoring financial statements and scrutinizing account activity can help individuals detect any suspicious or fraudulent transactions promptly. Additionally, leveraging security software, such as antivirus tools and ad blockers, provides an added layer of protection against phishing attempts and malicious online activities. By implementing these proactive measures, individuals can bolster their defenses against phishing attacks and safeguard their personal information from cyber threats.
Innovative Solutions to Prevent Phishing Attacks
Innovative solutions are continuously being developed to combat the pervasive threat of phishing attacks. One such solution is the implementation of advanced machine learning (ML) algorithms. By leveraging machine learning technology, organizations can analyze vast amounts of data to identify patterns and anomalies indicative of phishing attempts. These algorithms can proactively detect suspicious behavior and phishing indicators, enabling security teams to respond swiftly and effectively to potential threats.
Another promising innovation in the fight against phishing attacks is the development of behavioral analytics tools. These tools monitor user behavior and identify deviations from normal patterns, flagging potential phishing attempts in real-time. By analyzing user interactions with emails, websites, and applications, behavioral analytics platforms can detect anomalies indicative of phishing behavior, such as clicking on suspicious links or entering credentials into phishing websites. This proactive approach empowers organizations to thwart phishing attacks before they can inflict damage.
Sanction Scanner's AML Name Screening Tool
Sanction Scanner, a leading developer of AML compliance software, offers an advanced AML Name Screening Tool to enhance organizations' defense against financial crime. By automating the AML compliance process, organizations can ensure regulatory compliance and mitigate the risk of inadvertently facilitating money laundering or terrorist financing activities. Sanction Scanner's AML Name Screening Tool provides a comprehensive and efficient solution to safeguarding businesses against financial crime while streamlining compliance operations. To tear the net of phishing, contact us or request a demo today.